Showing posts with label security. Show all posts
Showing posts with label security. Show all posts
Friday, 8 November 2013
Russia: Chinese planting hidden chips in Irons & electric kettles which serve malware in systems
Labels:
Chinese Hackers,
Cyber Criminal,
cyber espionage,
Electric Iron,
exploit,
Hackers,
hardware hacking,
Hardware Trojan,
Malware,
Russian hackers,
security,
spying,
state sponsored attack,
vulnerability,
Wikileaks
Saturday, 2 November 2013
NSA leaker Edward Snowden gets job in a major Russian website
The NSA leaker Edward Snowden got a job after three months of his shipment to Russia. He got the job in a major Russian website, his lawyer said Thursday.
Edward Snowden will start working at a big Russian company on Friday, November 1. His job will be to support and develop a major Russian website,”lawyer said.
Asking upon the company’s name in which Snowden got job, lawyer didn’t disclose that, citing security concerns.
Speculation over Snowden’s new employer centred on the Russian equivalent of Facebook, Vkontakte, whose charismatic founder Pavel Durov publicly offered Snowden a post in August.
Right now two major Russian internet companies—yandex.ru and Mail.Ru Group said, “No, we didn’t hire Snowden.”
According to Snowden’s lawyer, he was running out of money that’ why he need a job.
After the revelation of secret documents of NSA, he was on a year temporary asylum in Russia.
Snowden spent more than a month in a Moscow airport before receiving a year’s temporary asylum and heading to a secret address.
Snowden supporter website also has raised $49,000 in donations.
Wednesday, 30 October 2013
iOS apps vulnerable to HTTP Request Hijacking attacks over WiFi

Speaking about the issue at RSA Conference Europe 2013 in Amsterdam, researchers have provided details on this vulnerability, which stems from a commonly used approach to URL caching.
Demonstration shows that insecure public networks can also provide stealth access to our iOS apps to potential attackers using HTTP request hijacking methods.
Demonstration shows that insecure public networks can also provide stealth access to our iOS apps to potential attackers using HTTP request hijacking methods.
The researchers put together a short video demonstrating, in which they use what is called a 301 directive to redirect the traffic flow from an app to an app maker’s server to the attacker’s server.
There are two limitations also, that the attacker needs to be physically near the victim for the initial poisoning to perform this attack and the flaw works only against HTTP traffic.
“A victim walks into Starbucks, connects to the Wi-Fi and uses her favorite apps,” explains an example. “Everything looks and behaves as normal, however an attacker is sitting at a nearby table and performs a silent HRH attack on her apps. The next day, she wakes up at home and logs in to read the news, but she’s now reading the attacker’s news!”
They estimate that at least 10,000 iOS apps in the Apple App Store are vulnerable to the hack. As a result, apps that display news, stock quotes, social media content, or even some online banking details can be manipulated to display fraudulent information and intercept data sent by the end user.
Victims can uninstall apps to scrub their devices clean, and Skycure has released app code that prevents the web caching from taking place. It may be a while until developers can get this fix implemented, so connect to those public networks with extreme caution.
Labels:
account Hijack,
Anonymous,
Apple,
apps security,
cyber attack,
Hackers,
hacking news,
hacking passwords,
iOS,
iPhone,
Malware,
Man-in-the-Browser,
mobile security,
security,
vulnerability,
Wikileaks
Wednesday, 16 October 2013
Hackers breach PureVPN website by exploiting a zero-day WHMCS vulnerability
"We are no longer able to run an anonymization service due to legal issues we are facing" The fake email reads.
"We had to handover all customer’s information to the authorities unfortunately. They might contact you if they need any details about the case they are working on. The following information was handed over: your name, billing address and phone number provided during purchase and any documents we had on file (for example scan of your ID or driver’s license if you have provided these to our billing department)."
However, the Co-founder ,Uzair Gadit, said in the official blog post that the email is fake and confirmed the purevpn website hit by a security breach.
Hackers exploited a vulnerability in 3rd party application WHMCS and compromised the email IDs and names of registered users.
"We repeat no billing information such as Credit Card or other sensitive personal information was compromised." The blog post reads.
Tuesday, 15 October 2013
Vulnerability in WhatsApp allows decrypting user messages
A serious vulnerability in WhatsApp allows anyone who is able to eavesdrop on WhatsApp connection to decrypt users' messages.
Whatsapp, the mobile application for instant messaging platform has become one of the main communication tools of the present day and its popularity makes it attractive for security researchers and hackers.
This time it is debated in the protection of the messages exchanged through the application, thanks to a vulnerability in the crypto implementation they can be intercepted by an attacker.
Thijs Alkemade is a computer science student at Utrecht University in The Netherlands who works on the open source Adium instant messaging project, during its research activity he disclosed a serious issue in the encryption used to secure WhatsApp messages.
In the post titled "Piercing Through WhatsApp’s Encryption" Alkemade remarked that Whatsapp has been plagued by numerous security issues recently, easily stolen passwords, unencrypted messages and even a website that can change anyone’s status.
"You should assume that anyone who is able to eavesdrop on your WhatsApp connection is capable of decrypting your messages, given enough effort. You should consider all your previous WhatsApp conversations compromised. There is nothing a WhatsApp user can do about this but expect to stop using it until the developers can update it." states the researcher.
An attacker sniffing a WhatsApp conversation is able to recover most of the plaintext bytes sent, WhatsApp uses RC4 software stream cipher to generate a stream of bytes that are encrypted with the XOR additive cipher.

The mistakes are:
- The same encryption key in both directions
- The same HMAC key in both directions
Below the trick used by the researcher to reveal the messages sent with WhatsApp exploiting first issue:
WhatsApp adopts the same key for the incoming and the outgoing RC4 stream, "we know that ciphertext byte i on the incoming stream xored with ciphertext byte i on the outgoing stream will be equal to xoring plaintext byte i on the incoming stream with plaintext byte i of the outgoing stream. By xoring this with either of the plaintext bytes, we can uncover the other byte."
The technique doesn't directly reveal all bytes but works in many cases, another element that advantage the attacker is that messages follow the same structure and are easy to predict starting from the portion of plaintext that is disclosed.
The second issue related to the HMAC id more difficult to exploit, Alkemade said WhatsApp also uses the same HMAC key in both directions, another implementation error that puts messages at risk, but is more difficult to exploit.
The MAC is used to detect data alteration but it is not enough to detect all forms of tampering, the attacker potentially could manipulate any message.
"TLS counters this by including a sequence number in the plaintext of every message and by using a different key for the HMAC for messages from the server to the client and for messages from the client to the server. WhatsApp does not use such a sequence counter and it reuses the key used for RC4 for the HMAC."
Alkemade is very critical to the development team of the popular platform:
“There are many pitfalls when developing a streaming encryption protocol. Considering they don’t know how to use a xor correctly, maybe the WhatsApp developers should stop trying to do this themselves and accept the solution that has been reviewed, updated and fixed for more than 15 years, like TLS,” he said.
I agree with the thinking of the researcher, security for applications such as WhatsApp is crucial given its level of penetration, it is true that the interest of the scientific community and cybercrime will surely lead them to discover new vulnerabilities to which WhatsApp have to provide a quick solution.
Alkemade confirmed that there is no remediation for the flaw in this moment, that's why he suggest to stop using WhatsApp until developers produce a patch.
Labels:
Anonymous,
cipher,
cyber attack,
decrypting,
encrypted message,
encryption,
exploit,
exploit code,
hack,
Hacking,
hacking WhatsApp,
Malware,
mobile hacking,
security,
sniffing,
vulnerability
Tuesday, 8 October 2013
Chinese hackers miss Google network, but the checks go on
Google
exec Schmidt says U.S. government networks are in danger 'because no
one is there' during the shutdown to stop hackers - See more at:
http://www.computerworld.com/s/article/9243040/Chinese_hackers_miss_Google_network_but_the_checks_go_on#sthash.a3ec9xiO.dpuf
Google exec Schmidt says U.S. government networks are in danger 'because no one is there' during the shutdown to stop hackers.
He put a question to an audience Gartner's Symposium ITxpo here on Monday. "Raise [your] hand if you're sure the Chinese are not inside your corporate network."
Many of the 8,500 attendees were in the hall to hear the question, but only five hands were raised. "Congratulations," Schmidt said from the stage.
Getting more serious, Schmidt lamented the open pathways in corporate networks, letting hackers slip in via NT servers.
Schmidt suggested a better network would eliminate the corporate intranet.
"We're going to have just a network. We're going to make sure that gaining access is application to application," he said.
In an interview on stage with Gartner analysts David Willis and Drue Reeves, Schmidt was asked whether he's sure that Chinese hackers haven't penetrated Google's corporate network.
"We're quite sure they are not right now," said Schmidt of the Chinese, "although every second we check." The audience chuckled.
"I can be quite sure that the Chinese are visiting the U.S. government at the moment because no one is there," said Schmidt, a reference to the federal government shutdown.
Major vendors, and other companies, have faced attacks from China.
Meanwhile, when asked about the security of mobile devices running the Google built Android operating system, Schmidt said "it's more secure than the iPhone."
Eric Schmidt, Google's executive chairman, put a question to an
audience Gartner's Symposium ITxpo here on Monday. "Raise [your] hand if
you're sure the Chinese are not inside your corporate network."
Many
of the 8,500 attendees were in the hall to hear the question, but only
five hands were raised. "Congratulations," Schmidt said from the stage. Getting more serious, Schmidt lamented the open pathways in corporate networks, letting hackers slip in via NT servers.
Schmidt suggested a better network would eliminate the corporate intranet.
"We're going to have just a network. We're going to make sure that gaining access is application to application," he said.
In an interview on stage with Gartner analysts David Willis and Drue Reeves, Schmidt was asked whether he's sure that Chinese hackers haven't penetrated Google's corporate network.
"We're quite sure they are not right now," said Schmidt of the Chinese, "although every second we check." The audience chuckled.
"I can be quite sure that the Chinese are visiting the U.S. government at the moment because no one is there," said Schmidt, a reference to the federal government shutdown.
Major vendors, and other companies, have faced attacks from China.
Meanwhile, when asked about the security of mobile devices running the Google built Android operating system, Schmidt said "it's more secure than the iPhone."
- See more at: http://www.computerworld.com/s/article/9243040/Chinese_hackers_miss_Google_network_but_the_checks_go_on#sthash.a3ec9xiO.dpuf
WhatsApp Website defaced by KDMS team
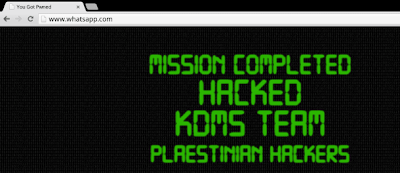 | |||||||||||
| WhatsApp Defaced Page |
The site showed a pro-Palestinian message at 2:40 a.m. PT Tuesday and was given the title "You Got Pwned." A group called KDMS Team claimed credit for the attack.
It wasn't immediately clear if there were any problems with WhatsApp's customer data or services. CNET contacted the company for comment and will update this story with its reply.
WhatsApp is used to send billions of messages a day using mobile apps.
Labels:
Anonymous,
Defacement,
Edward Snowden,
hack,
Hackers,
Hacking,
hacking news,
KDMS Team,
Malware,
News,
Palestine hacker,
security,
vulnerability,
WhatsApp,
WhatsApp Hacked,
wifi hacking,
Wikileaks
AVG Antivirus and Avira Websites defaced by Palestinian Hackers
 |
| AVG Antivirus Hack Screenshot |
The Website of Word's most popular Antivirus Firm - AVG were hacked this morning and defaced by a new Palestinian Hacker group - KDMS Team, affiliated with Anonymous Group.
The Defacement page titled 'You got Pwned', with Anonymous Logo and playing Palestinian national anthem in the page background, says:
we want to tell you that there is a land called Palestine on the earth
this land has been stolen by Zionist
do you know it ?
Palestinian people has the right to live in peace
Deserve to liberate their land and release all prisoners from israeli jails
we want peace and "There Is No Full Security We Can Catch You !"
UPDATE : Another Antivirus Firm 'AVIRA' website also defaced by hackers, just few minutes before.
 |
| Avira Website Defaced Page |
NETWORK SOLUTIONS, LLC is common Domain Registrar
for AVG, Avira and Whatsapp . Possibly, hacker compromised the Domain
Registrar and modifies the DNS settings to perform DNS Hijacking.
Labels:
Anonymous,
Antivirus,
AVG antivirus,
Defacement,
Edward Snowden,
hack,
Hackers,
Hacking,
hacking news,
KDMS Team,
Malware,
News,
Palestine hacker,
security,
vulnerability,
wifi hacking,
Wikileaks
More than 1000 Indian government websites hacked in the past three years
H4x0r HuSsY, famous for hacking Indian govt sites hit again. This time The official website of Public Works Department, Punjab with 10 other Indian Govt sites hacked by H4x0r HuSsY.
Anatomy of the attack on the Indian server is unknown. The hacked sites belongs to different name servers.
Two weeks before, Indian BioResource Information Network was hacked by the same hacker. h4x0r HuSsY also hacked Indian Goa Government Server last month.
rm -rf /planet/world/earth/india echo “The world is a better place now!”, The hacker wrote on the deface page.
Hacked Sites:
- pwdpunjab.gov.in/1337.html
- pscst.gov.in/1337.html
- http://jnvcalicut.gov.in/1337.html
- pbforestdevcorp.gov.in/1337.html
- prbdb.gov.in/1337.html
- mcludhiana.gov.in/1337.html
- esuwidha.mcludhiana.gov.in/upload
- www.jnvmahe.gov.in/123
- http://arogyasri.bbmp.gov.in/1337.html
- www.tnschools.gov.in/RMSA
- http://www.zone-h.org/mirror/id/20896977
- http://www.zone-h.org/mirror/id/20888936
- http://www.zone-h.org/mirror/id/20888938
- http://www.zone-h.org/mirror/id/20888937
- http://www.zone-h.org/mirror/id/20888935
- http://www.zone-h.org/mirror/id/20885932
- http://www.zone-h.org/mirror/id/20885850
- http://www.zone-h.org/mirror/id/20885463
- http://www.zone-h.org/mirror/id/20880949
Wednesday, 2 October 2013
16-Year School boy arrested for World's biggest cyber attack ever
16-Year-Old Teenager has been arrested over his alleged involvement in the World's biggest DDoS attacks against the Dutch anti-spam group Spamhaus.
The 16-year-old was detained by detectives at his home in south-west
London after “significant sums of money” were found to be “flowing
through his bank account”. He was also logged on to what officials say
were “various virtual systems and forums” & had his computers and
mobiles seized as officers worked through the night to secure potential
evidence.
The March 20 attack on Spamhaus has been dubbed as the “biggest cyber attack in the history of the Internet”
which saw server of the Dutch anti-spam organization being bombarded
with traffic in tune of 300 billion bits per second (300Gbps).
A DDoS attack takes place when hackers use an army of infected computers to send traffic to a server, causing a shutdown in the process.
It's
unclear what role the teenager played in the massive distributed denial
of service (DDoS) attack. The boy has been released on bail until later
this year. A 35-year-old Dutchman was detained and his computers, data
carriers and mobile phones were seized, local media speculates that the
person is none other than CyberBunker spokesman Sven Olaf Kamphuis.
Saturday, 7 September 2013
FBI Cyber Division put 'Syrian Electronic Army' Hackers in wanted list

The Syrian Electronic Army (SEA),
a pro-regime hacker group that emerged during Syrian anti-government
protests in 2011, and involved in cyber attacks against western media
organizations are now in the FBI's wanted list.
The Federal Bureau of Investigation has issued an alert warning of cyber
attacks by the Syrian Electronic Army and finally put them on its
radar. "The SEA'S primary capabilities include spear-phishing, web
defacements, and hijacking social media accounts to spread propaganda." they said. The FBI also has increased its surveillance of Syrians living in the US.
According to some anti-Assad activists, the group was founded by former
intelligence agents and hardcore Assad supporters. SEA had compromised
social media profiles for Western news organizations by sending fake email messages to news staff in an attempt to gain access to login credentials.

Most recently, the group grabbed international attention after commandeering the websites of the New York Times, Washington Post and this week the recruitment website for the US Marine Corps.
The group's was able to compromise the multiple Associated Press (AP) Twitter feeds, then using them to issue bogus messages, including the following alert on April 23 i.e. "Breaking: Two Explosions in the White House and Barack Obama is injured." In the wake of that tweet, the White House confirmed that the president was unharmed, that there had been no explosions and that the FBI was investigating the hoax tweets.
So how did the SEA get better in only a few months? ''I don't think it would be unreasonable to suspect someone more skilled is helping them out,'' says Adam Myers, vice president of intelligence for security firm CrowdStrike.
Is the Syrian Electronic Army based in Syria? After Syria reestablished its Internet connection last week, following a blackout that lasted approximately 24 hours. Security Experts noticed that Syrian Electronic Army Hackers were online on twitter. These kinds of cuts do not affect the terrorists operating in Syria as they have their own US-supplied communication equipment.
The Syrian Electronic Army has multiple domains seized by its domain registration firm. Interestingly, The Syrian Electronic Army's first domain name was registered by the Syrian Computer Society, hosted on the network of the Syrian government.
“Please maintain heightened awareness of your network traffic and take appropriate steps to maintain your network security,” the FBI memo said. FBI request anyone who suspects they're under attack to call its CyWatch division at 855-292-3937.
The group's was able to compromise the multiple Associated Press (AP) Twitter feeds, then using them to issue bogus messages, including the following alert on April 23 i.e. "Breaking: Two Explosions in the White House and Barack Obama is injured." In the wake of that tweet, the White House confirmed that the president was unharmed, that there had been no explosions and that the FBI was investigating the hoax tweets.
So how did the SEA get better in only a few months? ''I don't think it would be unreasonable to suspect someone more skilled is helping them out,'' says Adam Myers, vice president of intelligence for security firm CrowdStrike.
Is the Syrian Electronic Army based in Syria? After Syria reestablished its Internet connection last week, following a blackout that lasted approximately 24 hours. Security Experts noticed that Syrian Electronic Army Hackers were online on twitter. These kinds of cuts do not affect the terrorists operating in Syria as they have their own US-supplied communication equipment.
The Syrian Electronic Army has multiple domains seized by its domain registration firm. Interestingly, The Syrian Electronic Army's first domain name was registered by the Syrian Computer Society, hosted on the network of the Syrian government.
“Please maintain heightened awareness of your network traffic and take appropriate steps to maintain your network security,” the FBI memo said. FBI request anyone who suspects they're under attack to call its CyWatch division at 855-292-3937.
Labels:
cyber attacks,
Edward Snowden,
facebook,
FBI,
hack,
Hackers,
hacking news,
Intelligence,
News,
Phishing,
security,
surveillance,
Syrian Electronic Army,
the hacker news,
vulnerability,
Wikileaks
Researchers Discover 'Hesperbot' - A New and Potent Banking Trojan
Security firm ESET has discovered a new and effective banking trojan, targeting online banking users and designed to beat the mobile multi-factor authentication systems.
Hesperbot detected as Win32/Spy.Hesperbot is very identical to the infamous Zeus and SpyEye Banking Malwares and infects users in Turkey, the Czech Republic, Portugal, and the United Kingdom.
Trojan has functionalities such as keystroke logging, creation of screenshots and video capture, and setting up a remote proxy.
The attackers aim to obtain login credentials giving them access to the victim’s bank account and getting them to install a mobile component of the malware on their Symbian, Blackberry or Android phone.
The attackers aim to obtain login credentials giving them access to the victim’s bank account and getting them to install a mobile component of the malware on their Symbian, Blackberry or Android phone.
Some other advanced tricks are also included in this banking Trojan,
such as creating a hidden VNC server on the infected system and can do
network traffic interception with HTML injection capabilities.
The trojan also harvests email addresses from the infected system and
sends them to a remote server. It is possible that these collected
addresses were also targeted by the malware-spreading campaigns.
So far, the Trojan hasn't spread too far. The campaign was first detected in the Czech Republic where the attackers had used phishing
emails impersonating the country’s postal service. Armed with this
information, the crooks can try to log into victims' online bank
accounts to siphon off their cash.
As for the UK, a special variant of the malware has been created, but ESET said it could not provide any further detail on it.
Labels:
Anonymous,
banking malware,
cyber attack,
Edward Snowden,
facebook,
hack,
Hackers,
hacking news,
Hesperbot,
Malware,
News,
Phishing,
security,
SpyEye,
the hacker news,
Trojan,
vulnerability,
Wikileaks,
Zeus
Hacking Facebook to delete any account; Facebook again refuses to pay Bounty

In the past few days, Facebook refused to pay bounty to Khalil Shreateh, the security researcher who used the bug he discovered to post directly on Facebook CEO Mark Zuckerberg’s Timeline after Facebook Security rejected his attempts to report it.
Ehraz
Ahmed, an independent Security Researcher claimed that he reported a
critical vulnerability to the Facebook Security team, which allows the
attacker to delete any account from Facebook.
But Facebook refuses to Pay Bug Bounty, because he tested flaw once on his friend's account, "I
reported this bug to Facebook, I'm really not happy with them. After
waiting for such a long time for their reply, they denied it saying that
you used this bug only works for test accounts, where as I used it for
removing real accounts and now the vulnerability is also fixed after
their email." he said on his blog.
https://www.facebook.com/ajax/whitehat/delete_test_users.php? fb_dtsg=AQA1E-WE&selected_users[0]=[Victems Profile ID]&__user=[Attackers Profile ID]&__a=1Where selected_users[0] and __user parameters are vulnerable to run exploit.
Labels:
Anonymous,
bug bounty,
cyber attack,
delete account,
Edward Snowden,
facebook,
Facebook Hacking,
hack,
Hackers,
hacking news,
News,
password,
security,
the hacker news,
vulnerability,
Wikileaks
Secunia launches the next generation of Complete Patch Management: The Secunia CSI 7.0

Cybercrime costs organizations millions of dollars and to protect business from the consequences of security breaches, vulnerability
intelligence and patch management are basic necessities in the toolbox
of any IT team, as emphasized by organizations like the SANS Institute
and the National Institute of Standards and Technology under the US
Department of Commerce (NIST).
The Secunia CSI 7.0 is the Total Package: Vulnerability Intelligence, Vulnerability Scanning with Patch Creation and Patch Deployment Integration.
To help IT teams counter the threat, vulnerability research company
Secunia merges the in-house vulnerability expertise with a sophisticated
patch management
solution into the Secunia Corporate Software Inspector (CSI 7.0). The
foundation of the Secunia CSI is a unique combination of vulnerability
intelligence and vulnerability scanning, with patch creation and patch
deployment integration.
Labels:
Android,
Anonymous,
cyber attack,
Edward Snowden,
facebook,
hack,
Hackers,
hacking news,
News,
patch,
Patch Management,
scanner,
security,
Security tools,
the hacker news,
vulnerability,
Wikileaks
Friday, 6 September 2013
Fake 'Grand Theft Auto V' Torrent Spreads Malware

Excitement continues .. Rockstar Games schedule the release of latest The Grand Theft Auto series, GTA 5 on September 17, but Cyber Criminals has already released a fake version of GTA 5 contains malware on torrent networks.
Romanian security firm BitDefender issued warning that GTA V hasn’t
been leaked, and during installation you will be asked to complete a
survey and send off a text message to gain the serial number. You will
then be charged €1 per day on your phone bill and will be infected by a
virus.
The PC version has yet to be announced, so trying to install it on your
PC is a ridiculous idea; but that seems to be what a lot of people are
doing.
"The survey opens in a web browser and, therefore, is able to perform
a geographic redirect to the web page that corresponds to the area you
are located in," said, Bitdefender Senior E-Threat Analyst Bogdan Botezatu.
This malware is a generic Trojan Trojan.GenericKDV.1134859,
which can steal user information, tamper with system files or draft a
computer into a botnet. This will result in you being charged for
premium rate text messages sent by bogus firms.
The easiest way to avoid this malicious software is to not illegally
download copies of GTA V, especially when the game isn't yet launched.
Labels:
Anonymous,
Antivirus,
cyber attack,
Edward Snowden,
facebook,
game hack,
GTA 5,
hack,
Hackers,
hacking news,
Malware,
News,
security,
the hacker news,
Torrent,
Trojan,
vulnerability,
Wikileaks
Code-sharing site GitHub now offers two-factor authentication to its users
Code repository GitHub offers two-factor authentication
to beef up security around its users’ accounts. Github is a coding
repository where developers used to build their projects projects that
may turn out to be valued knowledgeable assets.
Two-Factor Authentication adds another layer of authentication to the
login process, Now users have to enter their username and password, and a
secret code in the second step, to complete the sign in. If a hacker
manages to steal a user's credentials through phishing or trojans,
cannot do anything, as they do need a second key to enter.
“We strongly urge you to turn on 2FA for the safety of your account, not only on GitHub, but on other websites that support it,” the company says. This two-factor authentication for Githu can be turned on in your account settings.
GitHub hit 3.5 million users’ landmark along with 6 million repositories
deposited on its 5th anniversary in April. Two-factor authentication
can protect you from phishing attacks, where hackers try to trick you
into giving over your information.
For receiving the second authentication factor, users can either choose
to receive it via a text message or can use dedicated authentication
mobile app i.e. Google Authenticator for Android/iPhone/BlackBerry or
Duo Mobile for Android/iPhone or Authenticator for Windows Phone 7.
Labels:
Anonymous,
cyber attack,
Edward Snowden,
exploit code,
facebook,
GitHub,
hack,
Hackers,
Hacking,
hacking news,
Malware,
News,
security,
security code,
Security News,
two factor authentication,
vulnerability,
Wikileaks
Saturday, 31 August 2013
Fear of NSA PRISM : Indian Government may ban US email services for official communication
The Indian Government is planning to ban the use of US based email
services like Gmail for official communications to increase the security
of confidential government information.
The recent disconcerting reports that that India was being spied upon by
American intelligence agencies has opened an all new chapter in the
cyber security space. As leaked by former US National Security Agency
contractor Edward Snowden, that NSA involved in widespread spying and
surveillance activities across the globe.
The Government plans to send a formal notification to about 500,000
employees across the country, asking them to stick to the official email
service provided by India's National Informatics Centre, Time of India Reported.
The fact that several government officers in top positions use their
Gmail IDs for official communications i.e. Several senior government
officials in India, including ministers of state for communications
& IT Milind Deora and Kruparani Killi, have their Gmail IDs listed
in government portals as their office email.
Last week, India's IT minister Kapil Sibal revealed that the new policy
will enforce rules such as use of static IP addresses, virtual private
networks and one-time passwords for accessing Indian government email
services on all Indian officials who are stationed abroad.
“All Indian missions will use NIC servers which are directly linked
to a server in India and that will keep government information safe.” Sibal said.
Labels:
Anonymous,
cyber attack,
Edward Snowden,
email hacking,
exploit code,
facebook,
gmail hacking,
hack,
Hackers,
hacking news,
indian government,
News,
NSA,
PRISM,
security,
Security News,
vulnerability,
Wikileaks
Thursday, 29 August 2013
Apple Patents Tech Allowing Cops To Remotely Switch Off Their Devices
Recently, The Social Media is buzzing over reports that Apple has
invented a new technology that now can Switch off iPhone Camera and
Wi-Fi, when entering a 'sensitive area'. Technology would broadcast a
signal to automatically shut down Smartphone features, or even the
entire phone.
Yes ! It's true, On June 2008 - Apple filed a patent (U.S. Patent No. 8,254,902) - titles “Apparatus and methods for enforcement of policies upon a wireless device” that defines the ability of U.S. Government to remotely disable certain functions of a device without user consent.
All they need to do is decide that a public gathering or venue is deemed
sensitive and needs to be protected from externalities. Is it not a
shame that you can't take a photo of the police officer beating a man in
the street because your oppressive government remotely disabled your
Smartphone camera? Civil liberties campaigners fear it could be misused
by the authorities to silence 'awkward citizens'.
Apple insists that the affected locations are normally cinemas, theaters
and concert grounds, but Apple admits it could also be used in covert
police or government operations that may need complete blackout
conditions.
"This technology would be a dangerous power to place in the hands of the government," Kurt Opsahl, a civil liberties lawyer at Electronic Frontier Foundation (EFF). "The
government shutting down iPhone cameras and connectivity in order to
prevent photos of political activity or the organization of the event
would constitute a prior restraint on the free speech rights of every
person affected, whether they're an activist or an observer" he added.
Apple also says that the user can be given a choice to approve changes being sent remotely, however one cannot rule out the possibility of some changes being applied to the device without user consent.
Apple also says that the user can be given a choice to approve changes being sent remotely, however one cannot rule out the possibility of some changes being applied to the device without user consent.
Labels:
Anonymous,
Apple,
camera hack,
Edward Snowden,
facebook,
hack,
hacking news,
iPhone,
News,
privacy,
security,
Security News,
spying,
surveillance,
U.S. government,
vulnerability,
Wikileaks
China hit by DDoS attack causes Internet inaccessible for hours
During the weekend China's Internet was taken down by a powerful distributed denial of service (DDoS) attack on the .cn domain slowed and blocked Internet access inaccessibility for hours.
Security expert clarified
that China could have been perpetrated by sophisticated hackers or by a
single individual. The China Internet Network Information Center [CINIC] reported that the attack began at 02:00 local time on Sunday with a peek at 04:00 that made it the largest DDoS attack the country’s networks have ever faced. The CCINIC is responsible for registering sites in the .cn domain.
Before malicious coders can launch a DDoS attack, they must infect the
computers of unsuspecting users, often by tricking people into
installing malware on their computers.
The China Internet Network Information Center confirmed the attack with
an official statement informing internet users that it is gradually
restoring web services and that will operate to improve the security
level of the Internet infrastructure of the country to prevent and
mitigate further attacks.
Following the translated announcement: "8 May 25 at 0:00 or
so, the State DNS node Denial of Service attacks, the China Internet
Network Information Center disposal, to 2 pm, the service is restored to
normal, early morning 3 through the official micro notice. Morning four
o'clock, the state once again under DNS node biggest ever denial of
service attacks, some websites analytical affected, leading to slow or
interrupt access.
In the notice, the attack continues, national domain name resolution
services have been gradually restored. Ministry of Industry and
Information Technology launched the "Domain Name System Security
specific contingency plans" to further the protection of national domain
name resolution services. China Internet Network Information Center,
the affected user apologized to launch cyber attacks on the Internet
stable behavior affect condemned. China Internet Network Information
Center will work with the sector to work together to continue to enhance
the service capabilities."
The Wall Street Journal was the first media agency that reported the
important outage, the official source of Chinese Government confirmed
that its network suffered the biggest distributed denial-of-service
attack ever.
It's not currently known who attacked the Chinese domain or the
motivations, CloudFlare CEO Matthew Prince said that there is no
certainty that behind the attack there is a group of hackers, he added
that "it may have well been a single individual".
Labels:
Anonymous,
Chinese Hackers,
cyber attack,
ddos attack,
Edward Snowden,
exploit code,
facebook,
hack,
Hacking,
hacking news,
Malware,
News,
security,
Security News,
vulnerability,
Wikileaks
FBI used Anonymous to attack foreign government systems, claims jailed hacker Hammond
Sentencing for former LulzSec leader Hector Xavier Monsegur, better known as "Sabu" ,
has again been delayed. Monsegur pleaded guilty to a dozen criminal
counts two years prior and stands to face more a maximum sentence of
more than 124 years.
Another Lulzsec Hacker Jeremy Hammond has claimed that the FBI used Sabu to coordinate attacks against foreign governments, by Anonymous hackers and Others.
The delays indicate
that the FBI is not extracting information from Monsegur and this could
mean that the hacker may be helping FBI with other covert operations as
Jeremy Hammond claims.
Jeremy Hammond, released a statement
on Thursday accusing the US government of asking Monsegur to encourage
fellow hacktivists to infiltrate foreign government entities.
“What many do not know is that Sabu was also used by his handlers to
facilitate the hacking of the targets of the government’s choosing
including numerous websites belonging to foreign governments”, Hammond said.
“What the United States could not accomplish legally, it used Sabu,
and by extension, me and my co-defendants, to accomplish illegally”, Hammond added.
"Why was the US using us to infiltrate the private networks of
foreign governments? What are they doing with the information we stole?
And will anyone in our government ever be held accountable for these
crimes?"
Hammond pleaded guilty in May to hacking private intelligence firm
Stratfor to expose millions of revelatory emails. The Illinois native
faces up to 10 years in prison when he is sentenced, scheduled for 15th
November.
Subscribe to:
Posts (Atom)











.jpg)


.jpg)
.jpg)